Hello all,
I'd like to introduce to you the upcoming addition to Ecsypno's product line: Codename RKN
Codename RKN is an automated WebApp I/O behavioral analysis (for reconnaissance and threat modelling) tool -- i.e. a penetration tester's best friend.
It is your manual webapp pentest assistant, allowing you to keep track of a Web application's attack surface as well as your progress traversing through it.
Core functionality
- Server-stack identification.
- Identify amount and types (link, form, cookie etc.) of inputs.
- Identify input characteristics, ex.:
- Data sinks -- Data lands in:
- HTML – reflected
- HTTP response headers – reflected
- JS runtime
- Whether or not an input triggers functionality on the server-side in a discernible manner.
- Whether or not an input triggers functionality on the client-side in a discernible manner.
- If an input appears to be non-functional server-side.
- If an input appears to be non-functional client-side.
- Parallel webapp scans.
- Multi-role scans.
- More to come.
Along with clever filtering, note-taking abilities and other utilities.
Walk-through

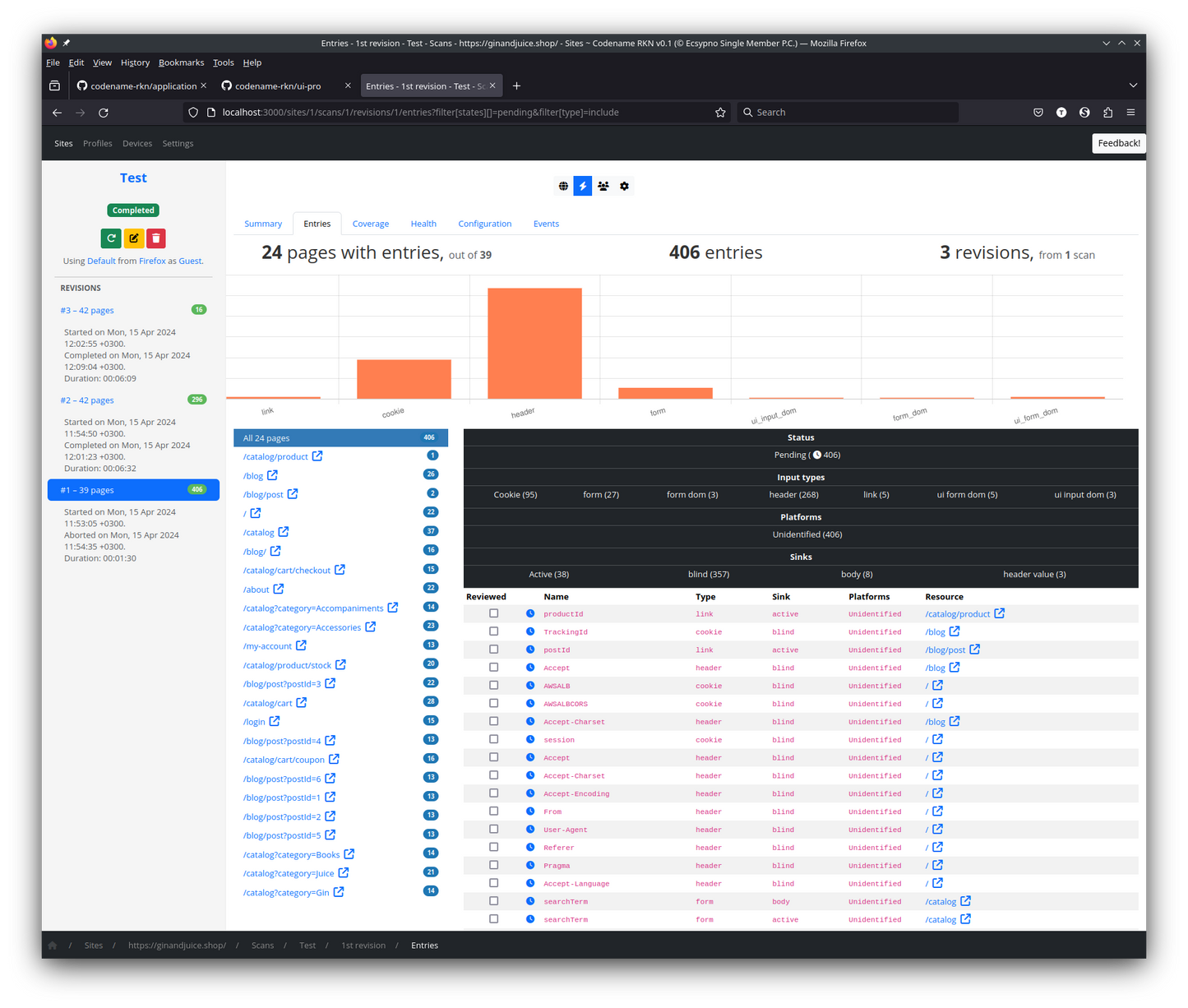
At this stage a scan is being performed and you get a live feed of I/O entries along with their characteristics.

Closer inspection of an I/O entry shows its behavior clearly.

Multiple repeats of the same scan performed and we're examining the entries of the first revision.

Immediate filtering allows you to narrow down entries based on I/O characteristics.

Again, examining an I/O entry.

This I/O entry allows us to place data into an HTTP header's value, interesting.

This entry's characteristics include Javascript/DOM involvement, let's move forward and see the I/O JS data-flow.

This is the coolest part!
You can trace the flow of data through Javascript and DOM.
Availability
I'm not sure when exactly Codename RKN will be available, but it should be soon-ish.
Cheers!
Tasos L.
